Jump Box Architecture
Questions?
Email our fast, friendly support if you have a question not covered here: [email protected].
Jump Box Architecture
What’s a Jump Box?
A Jump Box is a hardened server that you “jump” through in order to access other servers via SSH in a more protected network.
Sometimes called a bastion host or relay host, it’s simply a server that all of your users can log into and connect through as a relay server to connect to other servers.
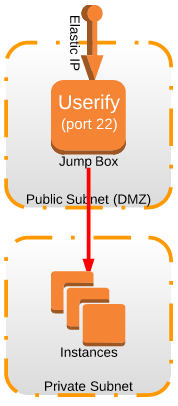
This article is geared for EC2 deployment inside a VPC but this design should work anywhere you can use Userify, such as in your own datacenter, Google, Azure, etc.
To build a jumpbox with Userify, just create a Jumpbox group and paste the regular Userify cloudinit script into the EC2 script box.
Creating a Jump Box
- Create a Userify Project called “Jumpbox” with a Userify Server Group called “Production”.
- Enable each of the users (only ‘user’ permission is needed) that will log into any server in that particular VPC or environment.
- For each group, launch a new jump box instance for each of your environments or VPC’s. (In a VPC, launch it in your public subnet. For EC2 Classic, launch it anywhere.)
- Paste in the UserData (CloudInit) script into the “Advanced” section on the “Instance Details” launch page and launch.
Lock down the other servers in the VPC and the Jumpbox (see below) as needed.
How to Log In
- SSH directly into your target box and use SSH’s
proxyjumptrick to “jump” through it:
ssh -J jumpbox targetserver
- You can also set up the same command in your .ssh/config file (on Linux, Mac, and Windows
running OpenSSH, and use plink if you are using Putty on Windows):
# .ssh/config
Host jumpbox
Hostname 10.22.1.22
Host target1
Proxyjump jumpbox
Host *
Username myuserifyusername
Port 22322
Note: older SSH clients may need to use the same trick with ProxyCommand.
Please email support if you have trouble setting this up.
Security Considerations and Tips
- Obviously your servers no longer need port 22 available to the outside world – but the Jump box still needs access to them.
- An effective Jump Box will simply contain the minimal software needed to run an SSH server and the Userify agent. Use whatever hardening techniques you prefer on this server.
- Users only need user level permissions on the jump box, unless they need to administer the jumpbox server itself. It’s recommended that everyone maintains user level permissions only – only grant root privileges to the jump box for a short period of time.
- Many users harden the instance, install fail2ban or denyhosts, change the default port 22 to an unusually high port (such as 31000), or even block access from unknown networks.
- You only need one Jumpbox for each network. Although you could create multiple for high availability in some circumstances, it might be easier to create an Auto-scaling Group (ASG) with a minimum and maximum size of one. The only requirement is that the Userify shim gets installed on it (see step 4), making it about the simplest ASG possible.
- You can lock down users by each of your environments (dev, staging, test) or for each of your regions (east, west, etc). Just add an extra Jump Box for each environment and configure your AWS security groups (firewall) to only allow SSH access from the Jumpbox for that environment.
- As with any Jump Box, users with ‘root’ permission can hijack other users’ session and possibly gain root access to servers they wouldn’t otherwise have access to.
Start managing your users and SSH keys in seconds Try for free